Recommendations From FBI Cyber Division on How to Reduce Risk from Ransomware Attacks
Ransomware continues to be a growing threat in 2022 given cybercriminals are constantly innovating and wreaking havoc within businesses. Worryingly the fiscal impact of a ransomware attack has more than doubled, increasing from $761,106 in 2020 to $1.85 million in 2021. This is due, in part, to the move by attackers to more advanced and complex targeted attacks that are harder to recover from. And in mid-sized organizations in thirty countries across the globe, 37% of organizations experienced a ransomware attack in the last 12 months.
Ransomware attacks against local government entities and the subsequent impacts are especially significant due to the public’s dependency on critical utilities, emergency services, educational facilities, and other services overseen by local governments, making them attractive targets for cyber criminals. Due to this the Federal Bureau of Investigation (FBI) has released a Private Industry Notification (PIN) to inform U.S. Government Facilities Sector partners of cyber actors conducting ransomware attacks on local government agencies that have resulted in disrupted operational services, risks to public safety, and financial losses.
We fully recommend local government officials, public service providers and IT professionals to review FBI PIN: Ransomware Attacks Straining Local US Governments.
From our perspective, the recommendations have some key takeaways, especially in relation to backups of data.
The two that jump off the page for me being:
- Maintain offline (i.e., physically disconnected) backups of data, and regularly test backup and restoration to safeguard continuity of operations or at least minimize potential downtime from an attack as well as protect against data losses. In cloud environments, consider leveraging native cloud service provider backup and restoration capabilities. To further secure cloud backups, consider separating account roles to prevent an account that manages the backups from being used to deny or degrade the backups should the account become compromised.
- Ensure all backup data is encrypted, immutable (i.e., cannot be altered or deleted), and covers the entire organization’s data infrastructure. Consider storing encryption keys outside the cloud. Cloud backups that are encrypted using a cloud key management service (KMS) could be affected should the cloud environment become compromised.
Catalogic DPX assists companies to deliver against these recommendations -, with DPX, you can have:
- Integrated ransomware protection – Backups are stored as immutable snapshots and can be offloaded as offline, air-gapped copies. DPX also provides real-time reporting to provide awareness ransomware could be present. We have some exciting enhancements coming with pro-active ransomware detection as we continue to push the boundaries to protect your data from ransomware.
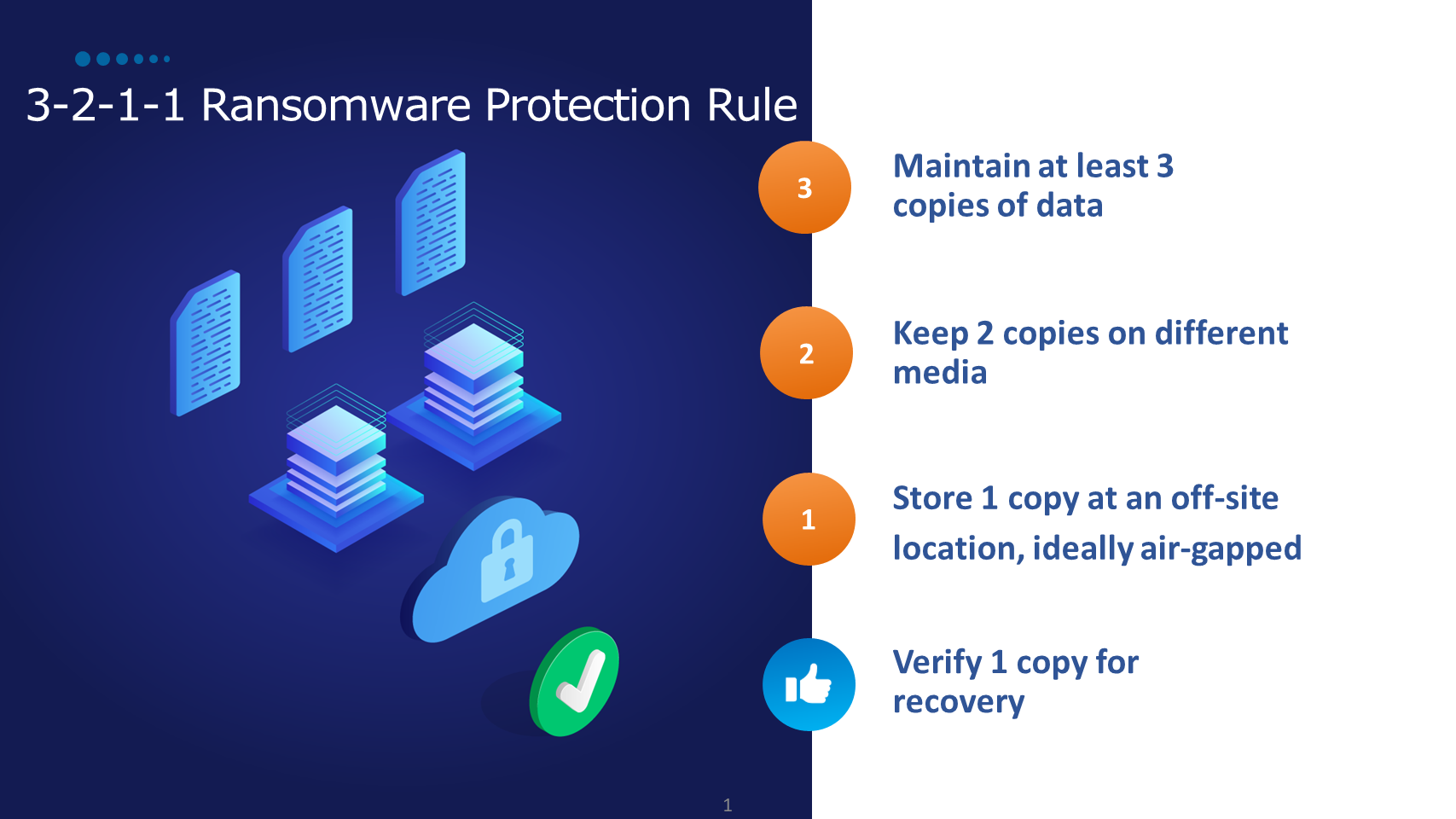
- Support for the 3-2-1-1 rule – Provides a robust data protection solution with verified scheduled recoveries for automated recovery testing.
- 3 copies of your data
- 2 copies stored on different storage media types
- 1 of the copies offsite or in the cloud on ideally immutable air-gapped or WORM media
- 1 verified as recoverable
- Encryption of backup data in transit and at rest – With DPX your data is encrypted over the network and at rest. DPX vStor volume encryption enables data at rest encryption on a volume in vStor Server, ensuring that if the underlying device is repurposed, returned, misplaced, or stolen the data cannot be accessed without the encryption key.
- Object Lock Support – In DPX 4.8 we introduced support for S3 Object Lock to set compliance and governance modes for cloud object storage. Once data is archived to the cloud, it cannot be modified or deleted, even by an administrator, protecting cloud backups against early deletion and providing an extra layer of protection against ransomware and data loss.
- Secure data protection for all your key systems – Quick, reliable backup for physical and virtual environments covering a wide range of enterprise applications.
- Secure Cloud integration – Makes it simple to send backup data to secured cloud object storage and recover from this data when needed.
- Rapid recovery and DR – Restore your systems in an instant with our patented instant virtualization technology. DPX delivers fast, reliable, granular point in time recovery with multiple recovery options.
- Hardware independence – Because DPX is a fully software-defined backup solution, you get the choice in terms of the servers and storage used. Servers can be physical or virtual, and the storage just needs to be block storage.
Catalogic or your favorite technology partner can deliver a secure data protection solution with instant recoverability to ensure you can protect your data from ransomware and recover in an instant when you need it.
On this topic we have recently published a detailed white paper: Ransomware – How to Protect and Recover Your Data from this Growing Threat, including a handy ransomware recovery checklist. Please do take a look at this handy resource.
With cyber-attacks proactively targeting local governments and public services, do not wait to further protect your organization’s backups from a ransomware attack. In all cases, it is not a matter of if, but when, an attack will occur.



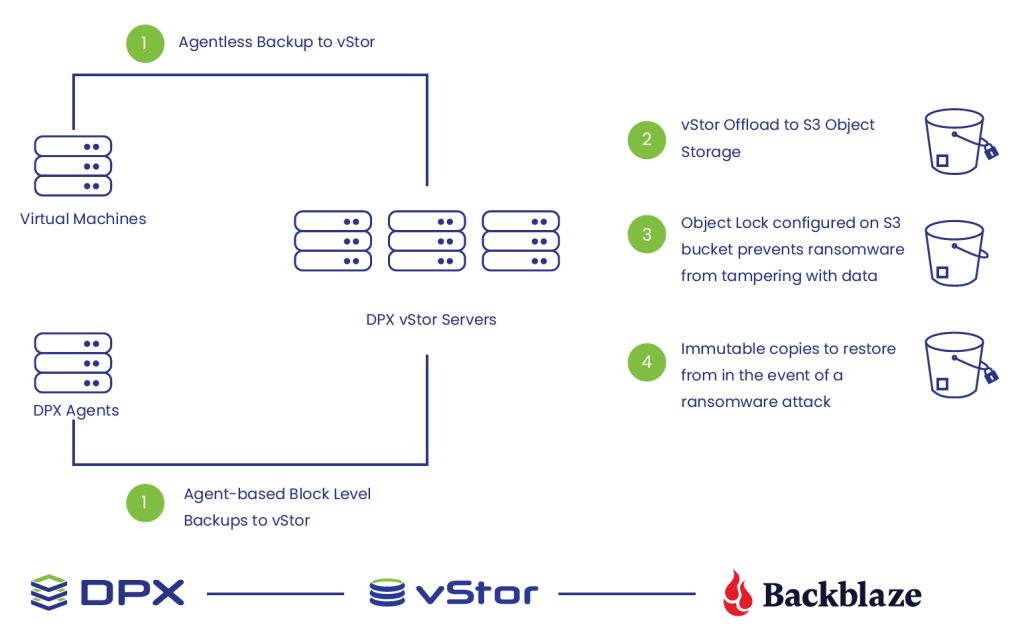


 storage with low data egress fees for storing DPX backups. Support for Backblaze B2 includes the ability to set S3 Object Lock modes and retention time
storage with low data egress fees for storing DPX backups. Support for Backblaze B2 includes the ability to set S3 Object Lock modes and retention time

 If backup data is one of the key targets, why do we see so many updates from backup and storage vendors on their ransomware protection? It’s because we all see the impact ransomware is having and we want to put businesses in a position where they can quickly recover from an attack without paying the ransom. Leaving your backup and storage infrastructure in the same security state as it was years ago means that you have a large attack surface with little likelihood that data recovery will be an option if you are hit with ransomware.
If backup data is one of the key targets, why do we see so many updates from backup and storage vendors on their ransomware protection? It’s because we all see the impact ransomware is having and we want to put businesses in a position where they can quickly recover from an attack without paying the ransom. Leaving your backup and storage infrastructure in the same security state as it was years ago means that you have a large attack surface with little likelihood that data recovery will be an option if you are hit with ransomware.