GuardMode verstehen: Verbesserter Ransomware-Schutz für Backups im Jahr 2025
Ransomware-Angriffe werden im Durchschnitt erst nach 7 bis 8 Tagen erkannt – und bis dahin könnten Ihre Backup-Dateien bereits kompromittiert sein. GuardMode von Catalogic ändert das, indem es Ihre Daten vor dem Backup überwacht, Bedrohungen frühzeitig erkennt und dabei hilft, nur die betroffenen Dateien wiederherzustellen, anstatt ganze Systeme zurückzusetzen.
Wenn Sie Backup-Administrator oder IT-Fachkraft mit Verantwortung für Datensicherheit sind, zeigt Ihnen dieser Beitrag, wie GuardMode funktioniert, welche Funktionen es bietet und wie es sich in Ihre bestehende Backup-Strategie integrieren lässt. In rund 10 Minuten erfahren Sie mehr über Erkennungsmethoden, Wiederherstellungsoptionen und praktische Vorteile.
Die aktuelle Herausforderung beim Ransomware-Schutz für Backups
Die Erkennung dauert zu lange
Die meisten Organisationen merken erst zu spät, dass sie Ziel eines Ransomware-Angriffs geworden sind. Studien zeigen, dass es im Jahr 2025 im Durchschnitt 7 bis 8 Tage dauert, bis eine aktive Infektion erkannt wird. In dieser Zeit kann sich die Schadsoftware im gesamten Netzwerk ausbreiten, Dateien verschlüsseln und unter Umständen Daten kompromittieren, die in regulären Backup-Zyklen enthalten sind.
Diese Verzögerung entsteht, weil herkömmliche Sicherheitswerkzeuge darauf fokussiert sind, Angriffe an Eintrittspunkten wie E-Mails oder Webbrowsern zu verhindern. Sobald Ransomware diese Schutzmaßnahmen umgeht, kann sie unbemerkt im Hintergrund agieren und nach und nach Dateien verschlüsseln, ohne sofortige Warnungen auszulösen.
Sicherheits- und Backup-Teams arbeiten isoliert
Zwischen den Tools des Security-Teams und der Backup-Infrastruktur besteht oft eine Trennung. Endpoint-Lösungen wie Antivirensoftware und Firewalls sind darauf ausgelegt, Bedrohungen vom Netzwerk fernzuhalten. Sie überwachen jedoch nicht explizit, was mit den Daten passiert, die von Backup-Systemen geschützt werden sollen.
Backup-Software hingegen konzentriert sich auf das verlässliche Kopieren und Speichern von Daten, analysiert jedoch in der Regel nicht, ob diese Daten kompromittiert wurden. Dies schafft eine Sicherheitslücke, bei der infizierte Dateien gemeinsam mit sauberen Daten gesichert werden und so die Wiederherstellungsmöglichkeiten verunreinigt werden.
Ransomware zielt auf Backup-Dateien
Moderne Ransomware ist so ausgereift, dass sie gezielt Backup-Dateien und -Systeme angreift. Angreifer wissen, dass Organisationen auf Backups zur Wiederherstellung angewiesen sind, und verschlüsseln daher gezielt Backup-Repositories, Schattenkopien und Wiederherstellungspunkte.
Wenn Ransomware Ihre Backup-Dateien erreicht, entfällt Ihre wichtigste Wiederherstellungsoption. Selbst wenn Sie den Angriff schnell erkennen, könnten Ihre aktuellen Backups bereits verschlüsselt oder korrumpiert sein – und Sie müssen auf ältere Kopien zurückgreifen.
Wiederherstellung wird zur Alles-oder-nichts-Entscheidung
Im Ernstfall stehen viele Unternehmen vor einer schwierigen Entscheidung: Alles aus einem sauberen Backup vor dem Angriff wiederherstellen oder versuchen, nur die betroffenen Dateien zu identifizieren und zurückzuspielen.
Die vollständige Systemwiederherstellung ist oft sicherer, aber auch zeitaufwändig und teuer. Alle Daten, die zwischen dem Backup und dem Angriff entstanden sind, gehen verloren. Dokumente müssen neu erstellt, Daten erneut eingegeben und Änderungen nachträglich umgesetzt werden.
Die Alternative – nur betroffene Dateien zu identifizieren – ist ohne geeignete Tools riskant. IT-Teams fehlt häufig der Einblick, welche Dateien verschlüsselt wurden, wann die Verschlüsselung begann und wie weit sich die Infektion ausgebreitet hat. Diese Unsicherheit führt oft dazu, dass eine vollständige Wiederherstellung gewählt wird, selbst wenn nur ein kleiner Teil der Daten betroffen war.
Ohne spezialisierte Erkennungs- und Nachverfolgungsfunktionen müssen Backup-Administratoren Entscheidungen auf unvollständiger Informationsbasis treffen – mit dem Risiko unnötiger Datenverluste und langer Ausfallzeiten.
Was ist GuardMode
Zweck und Designphilosophie
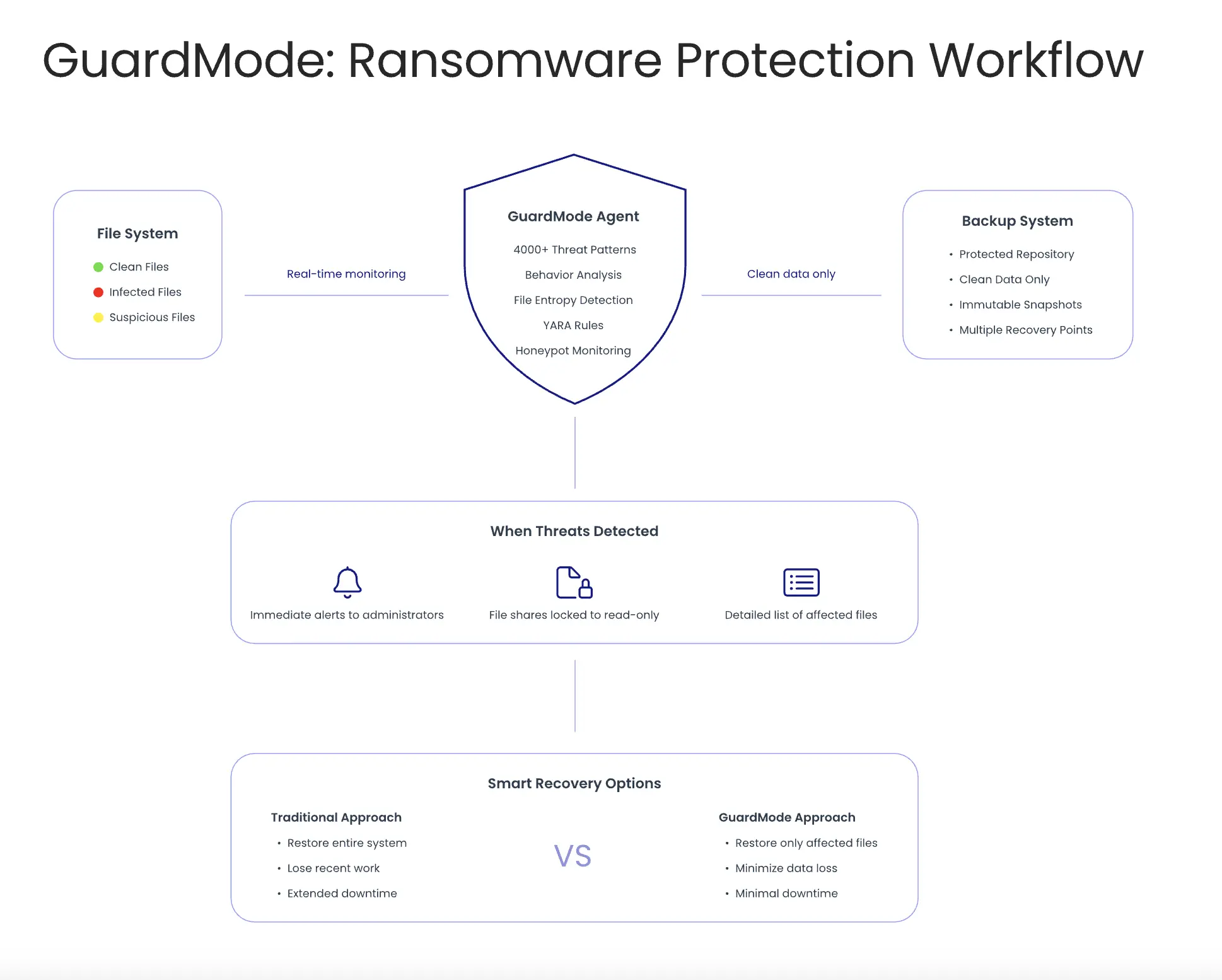
GuardMode ist ein System zur Erkennung und Abwehr von Ransomware, das speziell für Backup-Umgebungen entwickelt wurde und sich nahtlos in Catalogic DPX integriert. Im Gegensatz zu herkömmlicher Sicherheitssoftware, die Angriffe an Netzwerkeingängen abwehren soll, überwacht GuardMode Ihre Daten auf zwei Ebenen:
- Direkt vor dem Backup, um Bedrohungen zu erkennen, die anderen Schutzmechanismen entgangen sind
- Nach dem Backup, als zusätzliche Verteidigungsschicht für Systeme, die nicht vor dem Schutzprozess gescannt werden können
Das Konzept hinter GuardMode ist einfach: Backup-Administratoren brauchen eigene Sicherheitstools, die direkt mit ihren Backup-Prozessen und DPX-Workflows integriert sind. Anstatt sich auf das Security-Team zu verlassen, können Backup-Teams kompromittierte Daten erkennen und sofort innerhalb der gewohnten DPX-Oberfläche reagieren.
GuardMode arbeitet als integraler Bestandteil der Vor- und Nachsicherungs-Scanschichten von DPX. Es analysiert Dateien kontinuierlich, um ransomewaretypisches Verhalten zu erkennen, bevor die Daten im Backup landen. Die enge Integration verhindert, dass infizierte Dateien Ihre Wiederherstellungsoptionen beeinträchtigen, und bietet detaillierte Informationen über betroffene Dateien – alles über die vorhandene DPX-Konsole zugänglich.

Integration in Backup-Systeme
GuardMode funktioniert als Agent, den Sie auf Windows- und Linux-Servern installieren. Es überwacht Dateisysteme in Echtzeit und erkennt verdächtige Aktivitäten wie ungewöhnliche Dateioperationen oder schnelle Verschlüsselungsprozesse.
Das System ist offen konzipiert, bietet REST-APIs und unterstützt Standardprotokolle wie Syslog, um mit vorhandener Backup- und Sicherheitsinfrastruktur zu arbeiten. Bei verdächtigem Verhalten kann GuardMode automatisch Schutzmaßnahmen auslösen: Freigaben schreibschützen, sofort Snapshots erstellen oder Warnmeldungen an Backup- und Sicherheitsteams senden.
Wichtige Unterschiede zu herkömmlicher Sicherheitssoftware
Klassische Endpoint-Tools wie Antivirusprogramme und Firewalls blockieren Bedrohungen am Netzwerkeingang. Sie erkennen bekannte Malware-Signaturen und verhindern schädliche Downloads oder Anhänge.
GuardMode verfolgt einen anderen Ansatz und ergänzt diese Funktionen. Es geht davon aus, dass einige Bedrohungen durchkommen, und konzentriert sich stattdessen auf die durch Ransomware verursachten Auswirkungen – insbesondere auf Verschlüsselungs- und Änderungsmuster.
Durch diesen verhaltensbasierten Ansatz kann GuardMode auch neue Ransomware erkennen, die in keiner Signaturdatenbank steht.Es erkennt die Auswirkungen der Ransomware und nicht deren Code – und schützt so vor bekannten und unbekannten Bedrohungen.
Ein weiterer Unterschied liegt im Timing: Herkömmliche Tools erkennen Bedrohungen beim Eintritt. GuardMode überwacht kontinuierlich den Zustand Ihrer Datenumgebung und erkennt auch schleichende oder später auftretende Infektionen. Damit wird es zur echten Ransomware Protection für Backups.
Zielgruppe: Backup-Admins und IT-Teams
GuardMode wurde speziell für Backup-Administratoren entwickelt – also für jene, die dafür sorgen müssen, dass Daten im Notfall wiederhergestellt werden können. Während Security-Teams Angriffe verhindern wollen, brauchen Backup-Teams Tools, um auf bereits erfolgte Angriffe reagieren zu können.
Die Software bietet Backup-Admins Funktionen, die sie bisher nicht hatten:
- Transparenz zur Datenintegrität: Welche Dateien sind betroffen, welche sauber?
- Granulare Wiederherstellung: Nur kompromittierte Dateien wiederherstellen statt ganzer Systeme
- Integration in bestehende Workflows: Alarme und Reaktionen innerhalb der Backup-Prozesse
- Wiederherstellungshilfe: Schritt-für-Schritt-Anleitungen bei der Recovery
Auch IT-Teams profitieren: Sie erhalten detaillierte Infos zum Schadensausmaß und klare Wiederherstellungsoptionen – weniger Raten, weniger Stress. Gerade in hybriden Umgebungen mit On-Premises- und Cloud-Infrastruktur bietet GuardMode konsistenten Schutz für Dateifreigaben und Speichersysteme über alle Plattformen hinweg.
Fazit
GuardMode steht für den Wechsel von reaktiver zu proaktiver Datensicherung. Es gibt Backup-Teams die Werkzeuge an die Hand, um Bedrohungen frühzeitig zu erkennen und gezielt zu reagieren. Durch den klaren Fokus auf die Bedürfnisse von Backup-Admins schließt es eine kritische Lücke in vielen Ransomware-Abwehrstrategien und etabliert sich als effektive Ransomware Protection für Backups.
Im nächsten Blogbeitrag werfen wir einen genaueren Blick auf die technischen Funktionen von GuardMode – wir erkunden seine Erkennungsmethoden, Überwachungsfunktionen und Wiederherstellungsoptionen. Außerdem betrachten wir praxisnahe Implementierungsaspekte und reale Anwendungsfälle, die zeigen, wie Organisationen GuardMode einsetzen, um ihre Resilienz gegenüber Ransomware zu stärken.