Combatting Ransomware with Secure Backup and Recovery in an Instant
Ransomware is a growing threat that continues to wreak havoc within businesses as cybercriminals constantly innovate in terms of how they are executing attacks. One of the latest trends being seen is that attackers are proactively targeting and removing backup data. This is because if they encrypt or remove an organization’s backup data, then they have significantly enhanced the likelihood of the ransom being paid.
 If backup data is one of the key targets, why do we see so many updates from backup and storage vendors on their ransomware protection? It’s because we all see the impact ransomware is having and we want to put businesses in a position where they can quickly recover from an attack without paying the ransom. Leaving your backup and storage infrastructure in the same security state as it was years ago means that you have a large attack surface with little likelihood that data recovery will be an option if you are hit with ransomware.
If backup data is one of the key targets, why do we see so many updates from backup and storage vendors on their ransomware protection? It’s because we all see the impact ransomware is having and we want to put businesses in a position where they can quickly recover from an attack without paying the ransom. Leaving your backup and storage infrastructure in the same security state as it was years ago means that you have a large attack surface with little likelihood that data recovery will be an option if you are hit with ransomware.
But if you want to continue partying like it’s 1999 and ignore the advice to modernize and secure your backup data and storage environments, go ahead. Just realize when the party is over and the lights come on, your job or your business may no longer exist.
For IT backup and storage administrators, here are some key basic security and data protection principles to implement a robust backup and recovery solution to ensure data is kept safe from ransomware:
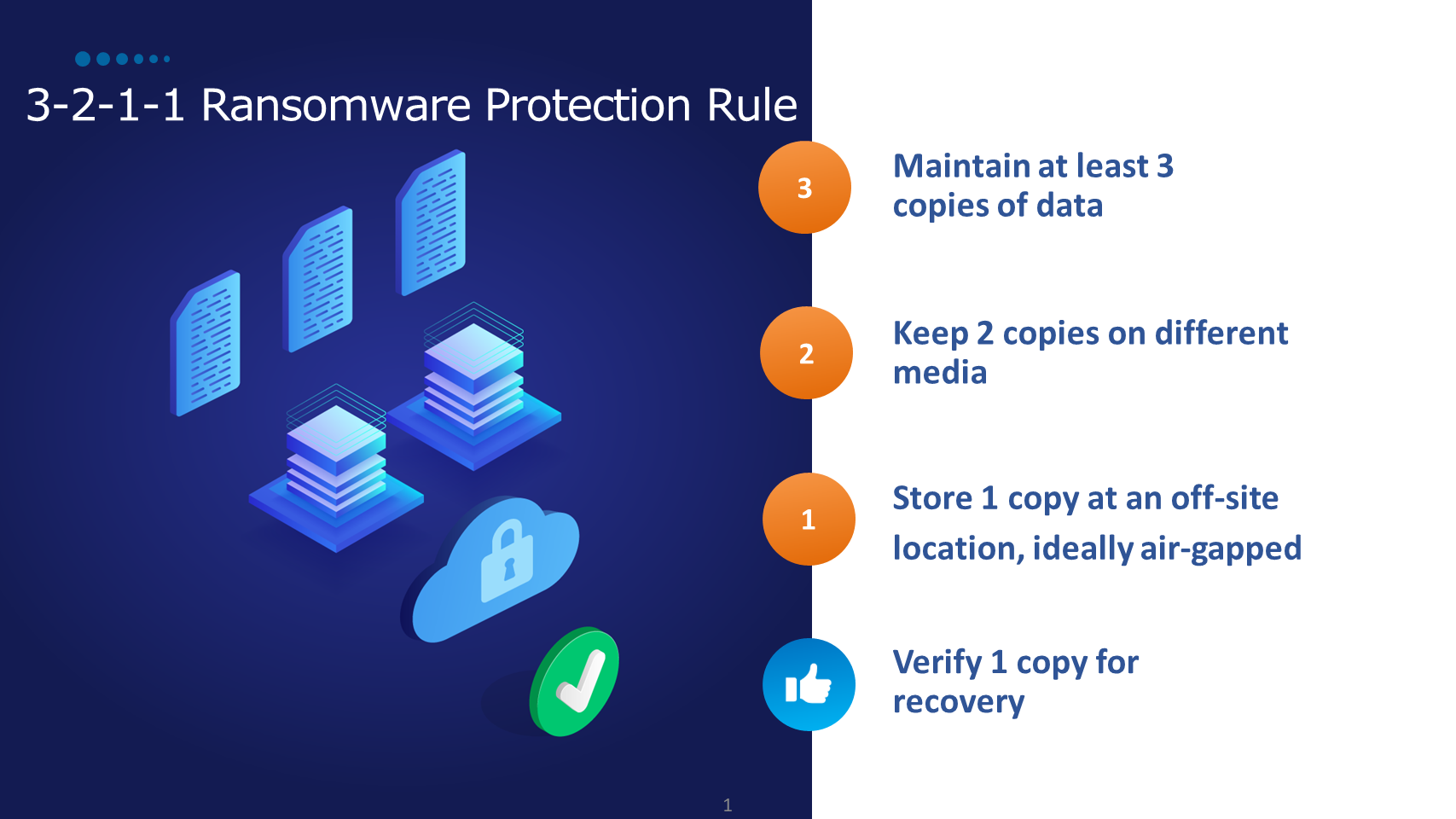
- Support for the 3-2-1-1 backup rule. 3-2-1-1 is a time-honoured strategy for data protection stating your business should have at least the following:
- 3 copies of your data
- 2 copies stored on different storage media types
- 1 of the copies offsite or in the cloud on ideally immutable air-gapped or WORM media
- 1 verified as recoverable
- Instant recoverability from immutable snapshots
- Granular point in time recovery with appropriate retention periods
- Application-aware backups with verification
- Real-time reporting to provide awareness ransomware could be present
If those basic security and data protection principles sound a tad overwhelming don’t worry, Catalogic has the people and software that can deliver a secure data protection solution with instant recoverability to ensure you can combat ransomware.
With Catalogic DPX you get:
- Integrated ransomware protection – Backups are stored as immutable snapshots and can be air-gapped. DPX also provides real-time reporting to provide awareness ransomware could be present. We have some exciting enhancements coming with pro-active ransomware detection as we continue to push the boundaries to protect your data from ransomware
- Support for the 3-2-1-1 rule – Provides a robust data protection solution with verified recovery
- Secure data protection for all your key systems – Quick, reliable backup for physical and virtual environments covering a wide range of enterprise applications
- Rapid recovery and DR – Restore your systems in an instant with our patented instant virtualization technology. DPX delivers fast, reliable, granular point in time recovery with multiple recovery options
- Hardware independence – Because DPX is a fully software-defined backup solution, you get the choice in terms of the servers and storage used. Servers can be physical or virtual, and the storage just needs to be block storage
- World-class support – The DPX support team is one of the best in the industry, with a standard customer satisfaction rating of over 95%
- Cloud integration – Makes it simple to send backup data to cloud object storage and recover from this data when needed
- Flexible and cost-effective licensing options – With subscription and perpetual options possible
We have recently published a detailed white paper: Ransomware – How to Protect and Recover Your Data from this Growing Threat, including a handy ransomware recovery checklist.
If you think your data protection solution isn’t ransomware recovery ready, please make your business leaders aware rather than having a bigger problem to sort out when attacked. Thanks for taking the time to read the blog. If you are interested in learning more about how we here at Catalogic can assist you in implementing enhanced data protection solutions and ensure recovery from ransomware is possible, please do get in touch.


