Tape Drives vs. Hard Drives: Is Tape Still a Viable Backup Option in 2025?
In the digital era, the importance of robust data storage and backup solutions cannot be overstated, particularly for businesses and individuals managing vast data volumes. Small and medium-sized businesses (SMBs) face a critical challenge in choosing how to securely store and protect their essential files. As data accumulates into terabytes over the years, identifying a dependable and economical backup option becomes imperative. Tape drives, a long-discussed method, prompt the question: Are they still a viable choice in 2025, or have hard drives and cloud backups emerged as superior alternatives?
Understanding the Basics of Tape Drives
Tape drives have been around for decades and were once the go-to storage solution for enterprise and archival data storage. The idea behind tape storage is simple: data is written sequentially to a magnetic tape, which can be stored and accessed when needed. In recent years, Linear Tape-Open (LTO) technology has become the standard in tape storage, with LTO-9 being the latest version, offering up to 18TB of native storage per tape.
Tape is designed for long-term storage. It’s not meant to be used as active, live storage, but instead serves as a cold backup—retrieved only when necessary. One of the biggest selling points of tape is its durability. Properly stored, tapes can last 20-30 years, making them ideal for long-term archiving.
Why Tape Drives Are Still Used in 2025
Despite the rise of SSDs, HDDs, and cloud storage, tape drives remain a favored solution for many enterprises, and even some SMBs, for a few key reasons:
- Cost Per Terabyte: Tapes are relatively inexpensive compared to SSDs and even some HDDs when you consider the cost per terabyte. While the initial investment in a tape drive can be steep (anywhere from $1,000 to $4,000), the cost of the tapes themselves is much lower than purchasing multiple hard drives, especially if you need to store large amounts of data.
- Longevity and Durability: Tape is known for its longevity. Once data is written to a tape, it can be stored in a climate-controlled environment for decades without risk of data loss due to drive failures or corruption that sometimes plague hard drives.
- Offline Storage and Security: Because tapes are physically disconnected from the network once they’re stored, they are immune to cyber-attacks like ransomware. For businesses that need to safeguard critical data, tape provides peace of mind as an offline backup that can’t be hacked or corrupted electronically.
- Capacity for Growth: LTO tapes offer large storage capacities, with LTO-9 capable of storing 18TB natively (45TB compressed). This scalability makes tape an attractive option for SMBs with expanding data needs but who may not want to constantly invest in new HDDs or increase cloud storage subscriptions.
 The Drawbacks of Tape Drives
The Drawbacks of Tape Drives
However, despite these benefits, there are some notable downsides to using tape as a backup medium for SMBs:
- Initial Costs and Complexity: While the per-tape cost is low, the tape drive itself is expensive. Additionally, setting up a tape backup system requires specialized hardware (often requiring a SAS PCIe card), which can be challenging for smaller businesses that lack an in-house IT department. Regular maintenance and cleaning of the drive are also necessary to ensure proper functioning.
- Slow Access Times: Unlike hard drives or cloud storage, tapes store data sequentially, which means retrieving files can take longer. If you need to restore specific data, especially in emergencies, tape drives may not be the fastest solution. It’s designed for long-term storage, not rapid, day-to-day access.
- Obsolescence of Drives: Tape drive technology moves fast, and newer generations may not be compatible with older tapes. For example, an LTO-9 drive can only read LTO-7 and LTO-8 tapes. If your drive fails in the future, finding a replacement could become a challenge if that specific technology has become outdated.
Hard Drives for Backup: A More Practical Choice?
On the other side of the debate, hard drives continue to be one of the most popular choices for SMB data storage and backups. Here’s why:
- Ease of Use: Hard drives are far more accessible and easier to set up than tape systems. Most external hard drives can be connected to any computer or server with minimal effort, making them a convenient choice for SMBs that lack specialized IT resources.
- Speed: When it comes to reading and writing data, HDDs are much faster than tape drives. If your business needs frequent access to archived data, HDDs are the better option. Additionally, with RAID configurations, businesses can benefit from redundancy and increased performance.
- Affordability: Hard drives are relatively cheap and getting more affordable each year. For businesses needing to store several terabytes of data, HDDs represent a reasonable investment. Larger drives are available at more affordable price points, and their plug-and-play nature makes them easy to scale up as data grows.
The Role of Cloud Backup Solutions
In 2025, cloud backup has become an essential part of the data storage conversation. Cloud solutions like Amazon S3 Glacier, Wasabi Hot Cloud Storage, Backblaze, or Microsoft Azure offer scalable and flexible storage options that eliminate the need for physical infrastructure. Cloud storage is highly secure, with encryption and redundancy protocols in place, but it comes with a recurring cost that increases as the amount of stored data grows.
For SMBs, cloud storage offers a middle-ground between tape and HDDs. It doesn’t require significant up-front investment like tape, and it doesn’t have the physical limitations of HDDs. The cloud also offers the advantage of being offsite, meaning data is protected from local disasters like fires or floods.
However, there are drawbacks to cloud solutions, such as egress fees when retrieving large amounts of data and concerns about data sovereignty. Furthermore, while cloud solutions are convenient, they are dependent on a strong, fast internet connection.
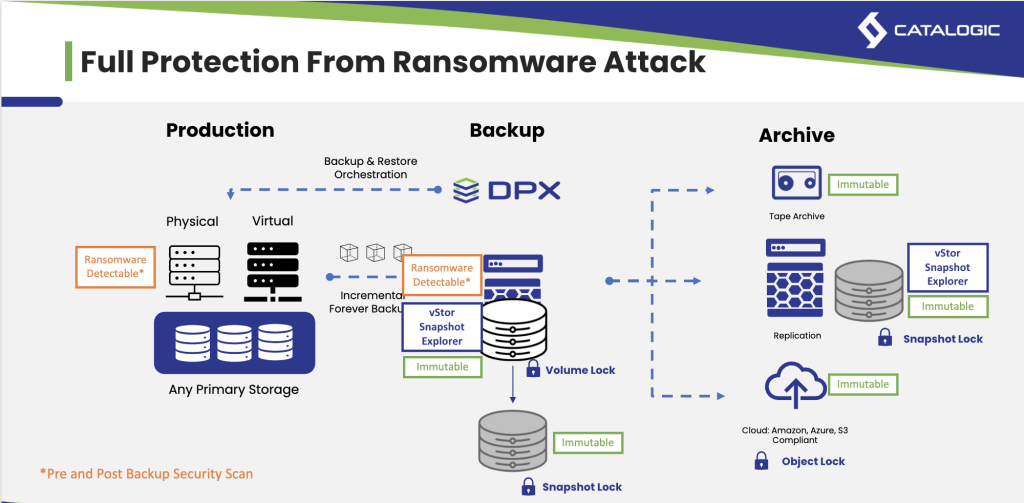
Catalogic DPX: Over 25 Years of Expertise in Tape Backup Solutions
For over 25 years, Catalogic DPX has been a trusted name in backup solutions, with a particular emphasis on tape backup technology. Designed to meet the evolving needs of small and medium-sized businesses (SMBs), Catalogic DPX offers unmatched compatibility and support for a wide range of tape devices, from legacy systems to the latest LTO-9 technology. This extensive experience allows businesses to seamlessly integrate both old and new hardware, ensuring continued access to critical data. The software’s robust features simplify tape management, reducing the complexity of handling multiple devices while minimizing troubleshooting efforts. With DPX, businesses can streamline their tape workflows, manage air-gapped copies for added security, and comply with data integrity regulations. Whether it’s NDMP backups, reducing backup times by up to 90%, or leveraging its patented block-level protection, Catalogic DPX provides a comprehensive, cost-effective solution to safeguard business data for the long term.
Choosing the Right Solution for Your Business
The choice between tape drives, hard drives, and cloud storage comes down to your business’s specific needs:
- For Large, Archival-Heavy Data: If you’re a business handling huge datasets and need to store them for long periods without frequent access, tape drives might still be a viable and cost-effective solution, especially if you have the budget to invest in the initial infrastructure.
- For Quick and Accessible Storage: If you require frequent access to your data or if your data changes regularly, HDDs are a better choice. They offer faster read/write times and are easier to manage.
- For Redundancy and Offsite Backup: Cloud storage provides flexibility and protection from physical damage. If you’re concerned about natural disasters or want to keep a copy of your data offsite without managing physical media, the cloud might be your best bet.
In conclusion, tape drives remain viable in 2025, especially for long-term archival purposes, but for most SMBs, a combination of HDDs and cloud storage likely offers the best balance of accessibility, cost, and security. Whether you’re storing cherished family memories or crucial business data, ensuring you have a reliable backup strategy is key to safeguarding your future.