Protect Your Scale Computing SC//Platform VMs with Catalogic DPX vPlus
With the ever-increasing risks of data mishaps, outages, or cyber threats, having a robust backup and recovery strategy is paramount. This is where Catalogic DPX vPlus steps in to offer a powerful data protection solution tailored specifically for Scale Computing SC/Platform environments.
Let’s delve into how Catalogic DPX vPlus provides seamless integration with Scale Computing, offering automated backups, flexible storage options, and reliable recovery steps. Discover the benefits of this dynamic duo in safeguarding your business data and ensuring uninterrupted operations in the face of any adversity.
Understanding the Scale Computing SC//Platform
Catalogic, a leading enterprise backup provider, offers seamless integration with the SC//Platform, providing a reliable safeguard against data mishaps.
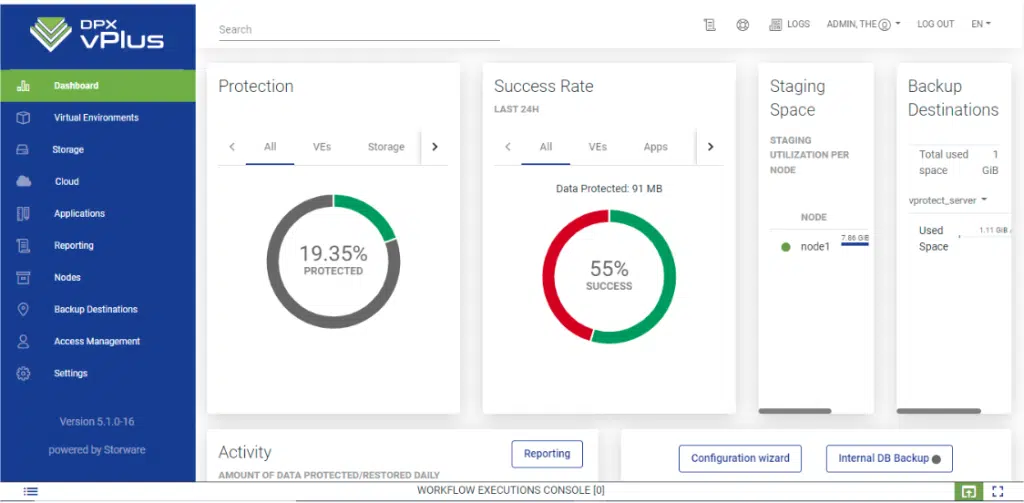
In terms of backup strategies, Catalogic DPX vPlus for SC//Platform offers a wide range of backup destinations, including disk attachment strategies and cloud storage options. It also provides flexible retention policies, allowing organizations to tailor their backup workflows to meet their specific needs.
The Crucial Role of SC//Platform Backup and Recovery
Protecting Against Data Loss
Ensuring Business Continuity
Adhering to Compliance Requirements
Mitigating the Risk of Malware Infection
Ensuring Granular Recovery
Integration with Scale Computing SC//Platform
Easy Integration
Automated Backup
Disaster Recovery
Flexible Storage Options:
Seamless Scale Computing Integration:
Backup strategies for Scale Computing SC//Platform
Full VM Backup
Incremental Backup
Offsite Backup
Snapshot-Based Backup
Flexible Storage Options
- Catalogic DPX vPlus provides a wide range of backup destination options, allowing you to choose the most suitable storage solution for your needs.
- You can store your backups on local storage, cloud storage, or even export them to a storage domain, providing flexibility and scalability.
Granular Recovery
- With Catalogic DPX vPlus, you can perform granular recovery of individual files or entire VMs, minimizing downtime and ensuring quick data restoration.
- This level of granularity allows you to recover specific data without the need to restore the entire backup, saving time and resources.
Remember, data protection is a fundamental aspect of an effective business continuity plan. With Catalogic DPX vPlus, you can confidently safeguard your Scale Computing SC//Platform VMs and mitigate the risk of data loss.
Conclusion
The integration of Catalogic DPX vPlus with the Scale Computing SC//Platform simplifies the backup process while accommodating diverse backup destination options, whether you choose local storage, cloud storage, or tape pool. Its granular recovery feature allows for the easy restoration of individual files or entire virtual machines, minimizing operational disruptions. Additionally, the rapid recovery capability of DPX vPlus significantly reduces the risk of financial loss and downtime by swiftly restoring your VMs.
The intuitive backup workflow and seamless integration with the SC//Platform make Catalogic DPX vPlus a manageable and effective solution for your data protection needs. By investing in Catalogic DPX vPlus, you are not only protecting your data against hardware failures, human errors, and natural disasters but also ensuring the continuous availability and safety of your valuable information.