Maximize Database Backup Efficiency with DPX vStor: Application-Consistent Protection for Oracle and SQL
In today’s data-centric world, protecting mission-critical databases such as Oracle, SQL, and others requires more than just speed and efficiency—it demands consistency and reliability. Catalogic’s DPX vStor, a software-defined backup appliance, stands out as a versatile and scalable solution capable of ensuring application-consistent backups for databases while also offering flexibility for DBAs to manage native database backups if preferred.
With its built-in features like deduplication, compression, snapshotting, and replication, DPX vStor can optimize your data protection strategy for databases, allowing for seamless integration with applications and custom approaches managed by database administrators (DBAs).
What is DPX vStor?
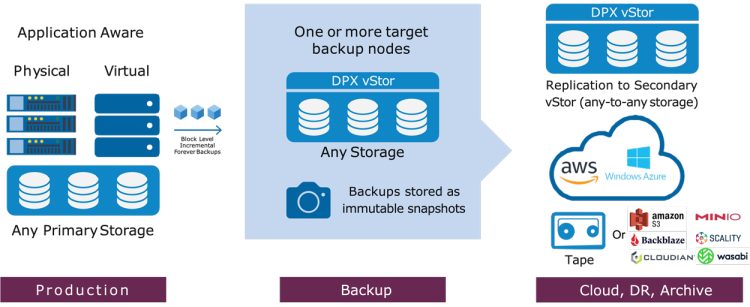
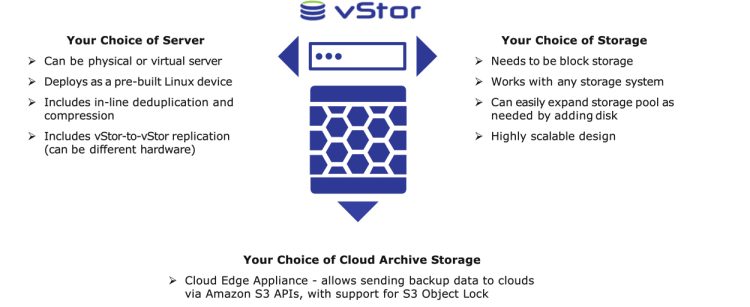
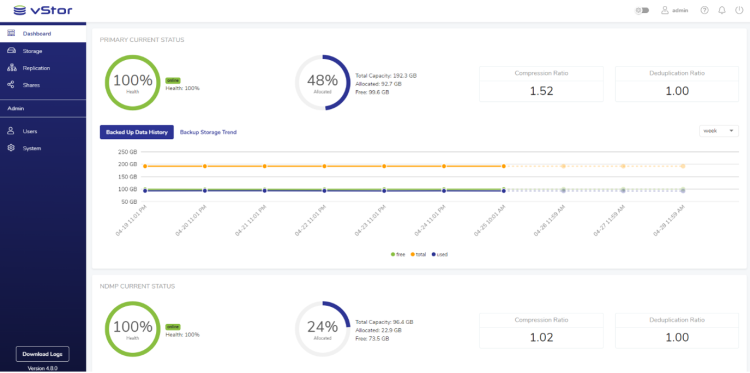
DPX vStor is a scalable, software-defined backup appliance that delivers comprehensive data protection, high storage efficiency, and rapid recovery. It combines deduplication, compression, snapshotting, and replication capabilities in a single platform, making it a go-to solution for protecting not just storing backups of VMs or physical servers but also databases such as Oracle and SQL.
Native and Application-Consistent Database Backups
Databases are at the heart of business operations, and ensuring their availability and consistency is crucial. DPX vStor provides two powerful approaches to database backups:
- DPX Application-Consistent Backups: DPX vStor can ensure that backups are application-consistent, meaning that database transactions are quiesced, and the data captured in the backup is in a consistent state. This ensures that when a restore is performed, the database can be recovered without the need for additional work or repairs, preserving data integrity and reducing recovery times.
- Native Database Backups: While DPX excels in providing application-consistent backups, some DBAs may prefer more granular control over their database backup processes, opting to use native database tools such as Oracle RMAN (Recovery Manager) or SQL Server’s backup utilities. DPX vStor supports this approach, enabling DBAs to retain control over native backups while still benefiting from vStor’s advanced features like deduplication, compression, snapshotting, and replication for optimized storage and protection.
Key Features of DPX vStor for Database Backups
- Application Consistency with Minimal Disruption: DPX integrates with Oracle, SQL, and other databases to drive application-consistent backups. This ensures that all database transactions are fully captured, providing a consistent point-in-time backup that requires minimal post-recovery intervention. It also allows for Instant Recovery of databases using the snapshot and mounting capabilities from the DPX vStor.
- Flexibility for DBAs: While application-consistent backups are often preferred for their automation and reliability, DPX vStor acknowledges that DBAs may prefer more direct control over their backups. By allowing for native database backups, DPX vStor ensures that DBAs can use the tools they’re most comfortable with, such as Oracle RMAN or SQL Server’s native backup utilities, while still leveraging the appliance’s advanced features.
- Deduplication and Compression for Storage Efficiency: DPX vStor’s deduplication and compression capabilities significantly reduce the storage footprint of database backups. By eliminating redundant data and compressing backup files, storage usage is optimized, and backup times are shortened—critical factors when dealing with large-scale databases.
- Immutable Backups with Snapshotting: DPX vStor’s built-in snapshotting capabilities enable immutable backups, meaning they cannot be altered once created. Immutability is crucial for protecting against data corruption, ransomware, or other cyber threats and ensuring the integrity and security of your backups.
- Replication for Disaster Recovery: With vStor, database backups can be replicated to a secondary site, providing a robust disaster recovery solution. Whether on-premises or in the cloud, replication ensures that a current, secure copy of your backups is always available, minimizing downtime in case of failure.
- Rapid Recovery and Reduced Backup Windows: DPX vStor ensures fast recovery times, whether for application-consistent or native backups, reducing business downtime. Additionally, thanks to deduplication, compression, and snapshotting, backup windows are shortened, allowing for efficient and fast backups without impacting database performance.
Why Choose DPX vStor for Database Backup?
By integrating application-consistent backups and supporting native backup processes, DPX vStor offers the best of both worlds. Whether your IT team prefers automated, application-consistent backups or your DBAs prefer to manage backups using native tools, DPX vStor has the flexibility to meet those needs. At the same time, with built-in data reduction technologies and the ability to create immutable snapshots, vStor ensures that backups are both storage-efficient and secure from tampering or ransomware.











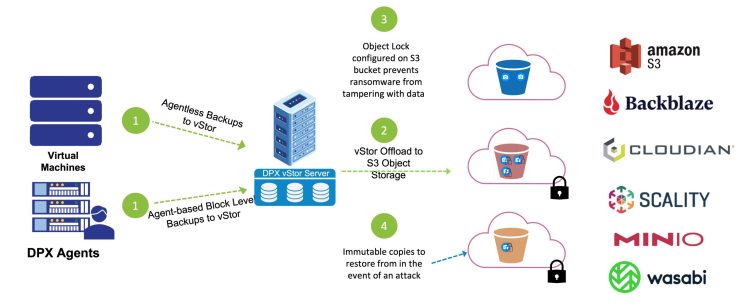


 If backup data is one of the key targets, why do we see so many updates from backup and storage vendors on their ransomware protection? It’s because we all see the impact ransomware is having and we want to put businesses in a position where they can quickly recover from an attack without paying the ransom. Leaving your backup and storage infrastructure in the same security state as it was years ago means that you have a large attack surface with little likelihood that data recovery will be an option if you are hit with ransomware.
If backup data is one of the key targets, why do we see so many updates from backup and storage vendors on their ransomware protection? It’s because we all see the impact ransomware is having and we want to put businesses in a position where they can quickly recover from an attack without paying the ransom. Leaving your backup and storage infrastructure in the same security state as it was years ago means that you have a large attack surface with little likelihood that data recovery will be an option if you are hit with ransomware.