Vorstellung Backup-Verifizierung in DPX 4.13
Wenn Sie dafür verantwortlich sind, Daten sicher zu halten – ob im IT‑Betrieb, in der Infrastrukturverwaltung oder in der Cybersicherheit – sind Backups Ihr Sicherheitsnetz. Sie greifen, wenn Systeme ausfallen, Dateien verschwinden oder Ransomware zuschlägt. Aber eines ist entscheidend: Sie müssen Verifizierungen durchführen. Nur weil ein Backup als „erfolgreich“ gemeldet wird, heißt das nicht, dass es auch wirklich wiederherstellbar ist. Viele Backup‑Systeme prüfen nicht, ob die Daten auch tatsächlich zurückgespielt werden können. Sie warnen nicht, wenn Dateien beschädigt oder unvollständig sind – oder schlimmer noch, bereits mit Malware verseucht. Und am Tag der Wiederherstellung stehen Sie ratlos da.
DPX 4.13 führt nun eine automatische Backup‑Verifizierung ein – für alle, die sich kein Rätselraten leisten können. IT‑Administratoren, System‑Ingenieure, Backup‑Operatoren und Cyber‑Security‑Teams erhalten Gewissheit – nicht nur Hoffnung –, dass ihre Backups funktionieren. Direkt nach jedem Backup läuft automatisch eine Verifizierung, inklusive integriertem Malware‑Scan, damit Probleme früh erkannt und behoben werden – noch bevor eine Wiederherstellung nötig wird.
Warum herkömmliche Backups nicht ausreichen
Ein grünes Licht im Backup‑Dashboard wirkt oft beruhigend, kann aber trügerisch sein. Viele Systeme melden nur, dass Daten kopiert wurden – nicht, ob das Backup auch wirklich wiederherstellbar ist. Wenn es beschädigt ist oder versteckte Malware enthält, merken Sie es erst beim Wiederherstellungstest – dann ist es zu spät.
DPX 4.13 geht dieses Problem aktiv an: Es prüft die Integrität des Backups und scannt auf Malware. So gewinnen Sie echte Sicherheit, dass Ihre Daten tatsächlich sauber und wiederherstellbar sind.
Was DPX 4.13 anders macht
DPX 4.13 führt eine automatische Backup‑Verifizierung mit zwei zentralen Schritten ein: Integritätsprüfung und Bedrohungsscans. Beides erfolgt direkt nach Abschluss des Backups – ganz ohne manuelle Eingriffe Ihres Teams.
Dateien‑System‑Prüfung
DPX mountet das Backup wie für eine vollständige Wiederherstellung. Anschließend werden Dateisystem, Partitionslayout und Zugriffsrechte geprüft. Wenn etwas nicht stimmt – etwa Datenkorruption, fehlende Rechte oder strukturelle Probleme – wird das sofort alarmiert.
Malware‑Scan (GuardMode)
Sobald das Backup die Integritätsprüfung bestanden hat, startet GuardMode einen Scan auf bekannte Malware-Signaturen und unregelmäßiges Dateiverhalten – etwa typische Merkmale von Ransomware oder schlafenden Bedrohungen.
Live‑Monitoring und Alarmierung
Jeder Schritt des Verifizierungsprozesses ist in Echtzeit sichtbar. Wenn die Verifizierung fehlschlägt oder eine Bedrohung entdeckt wird, erhält Ihr Team unmittelbar eine Benachrichtigung über das integrierte Alarmsystem.
Wo es funktioniert
DPX 4.13 unterstützt zwei Backup‑Typen von Haus aus:
VMware‑Backups
Für agentenlose VMware‑Jobs mountet und prüft DPX die VM‑Backups automatisiert – ganz ohne Agent auf den Gastsystemen. Mehrere Festplatten, komplexe Partitionen und verschiedene Dateisysteme werden nahtlos abgedeckt.
Block‑Level‑Backups
Die gleiche Verifizierungs‑Engine kommt auch bei physischen Server‑ oder Bare‑Metal‑Backups zum Einsatz. Egal welches Betriebssystem, Partitionsschema oder Wiederherstellungsformat – Sie erhalten überall dieselbe Validierung.
Wichtiger Hinweis: vStor erforderlich
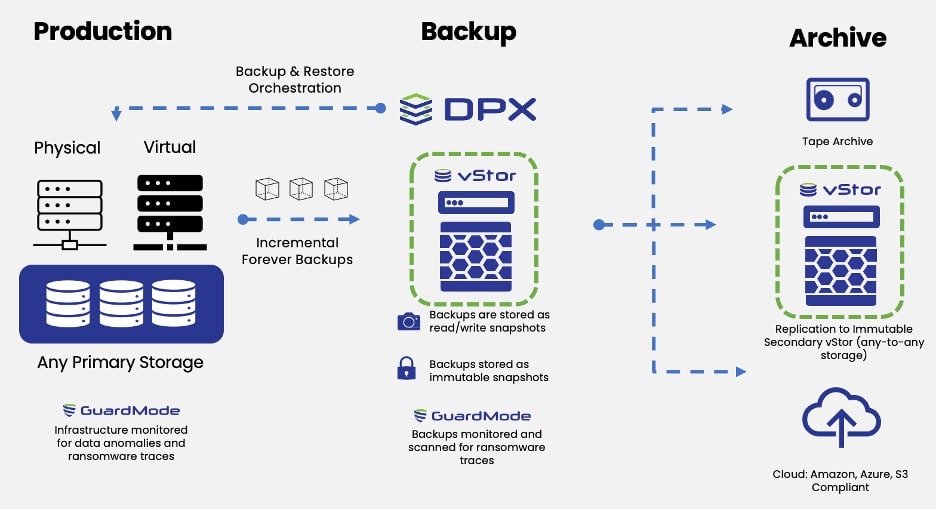
Diese neue Verifizierungsfunktion ist nur nutzbar, wenn Ihre Backups in Catalogics vStor gespeichert sind. Nur vStor bietet die nötige Mount‑Technologie, um Restore‑Simulationen und Scans durchzuführen. Wenn Sie ein anderes Storage‑Backend verwenden, müssen Sie Ihre Backups auf vStor migrieren, um diese Funktion nutzen zu können.
Die enge Integration mit vStor gewährleistet reibungslose Performance, schnelle Scans und verlässliche Ergebnisse – ohne Ihre Produktionssysteme zu belasten.
So funktioniert’s – ein Blick hinter die Kulissen
Nach Abschluss eines Backups läuft folgender Prozess automatisch ab:
- Backup ist abgeschlossen
- Verifizierung startet (vorausgesetzt aktiviert)
- DPX greift auf das Backup über vStor zu
- Dateien‑Systemprüfung – Integrität & Zugriffsrechte
- GuardMode‑Scan – Malware‑Erkennung (falls aktiviert)
- Ergebnisse erscheinen im Backup‑Job‑Bericht mit detaillierten Angaben
Wenn das Backup die Dateisystemprüfung nicht besteht, wird der Malware‑Scan übersprungen – so werden keine Ressourcen auf beschädigte Daten verschwendet. Alle Ergebnisse werden geloggt und können für Audits oder Compliance‑Zwecke exportiert werden.
Warum das im Alltag zählt
Risiko reduzieren
Die häufigsten Restore‑Fehler entstehen durch beschädigte Backups oder versteckte Malware. DPX 4.13 hilft, beides zu vermeiden. Es stellt sicher, dass Backups wiederherstellbar und frei von Bedrohungen sind. Für Unternehmen mit Compliance‑Anforderungen bieten die automatisierten Prüfungen und Audit‑Logs zusätzliche Sicherheit und Dokumentation.
Zeit sparen
Manuelle Restore‑Tests sind aufwendig und werden häufig übersprungen. Mit DPX 4.13 laufen sie automatisch im Hintergrund – ohne Eingriff Ihres Teams. Das System skaliert problemlos – egal, ob Sie 10 oder 10 000 Systeme sichern.
Das große Ganze: Von Hoffnung zur Sicherheit
Früher bedeutete Backup: „Wir hoffen, es funktioniert.“
Mit DPX 4.13 heißt es: „Wir wissen, dass es funktioniert.“
Es ist eine stille, aber wesentliche Weiterentwicklung Ihrer Daten‑Schutz‑Strategie. Der letzte Schritt der Datensicherung wird zu einem verlässlichen Schutzmechanismus – für das Wichtigste: Ruhe und Sicherheit. Wenn irgendwann etwas schiefgeht, greifen Sie auf ein getestetes, sauberes Backup zurück.
Coming Soon
DPX 4.13 erscheint im Sommer 2025. Wenn Sie bereits vStor mit DPX für VMware‑ oder Block‑Level‑Backups verwenden, ist die Aktivierung der Verifizierung einfach. Andernfalls ist jetzt ein guter Zeitpunkt, Ihre Backup‑Strategie neu zu bewerten. Können Sie Ihren Backups heute wirklich vertrauen? Wenn die Antwort kein eindeutiges „Ja“ ist, sollten Sie DPX 4.13 ernsthaft in Betracht ziehen.