Building a Reliable Backup Repository: Comparing Storage Types for 5-50TB of Data
 When setting up a secondary site for backups, selecting the right storage solution is crucial for both performance and reliability. With around 5-50TB of virtual machine (VM) data and a retention requirement of 30 days plus 12 monthly backups, the choice of backup repository storage type directly impacts efficiency, security, and scalability. Options like XFS, reFS, object storage, and DPX vStor offer different benefits, each suited to specific backup needs.
When setting up a secondary site for backups, selecting the right storage solution is crucial for both performance and reliability. With around 5-50TB of virtual machine (VM) data and a retention requirement of 30 days plus 12 monthly backups, the choice of backup repository storage type directly impacts efficiency, security, and scalability. Options like XFS, reFS, object storage, and DPX vStor offer different benefits, each suited to specific backup needs.
This article compares popular storage configurations for backup repositories, covering essential considerations like immutability, storage optimization, and scalability to help determine which solution best aligns with your requirements.
Key Considerations for Choosing Backup Repository Storage
A reliable backup repository for any environment should balance several key factors:
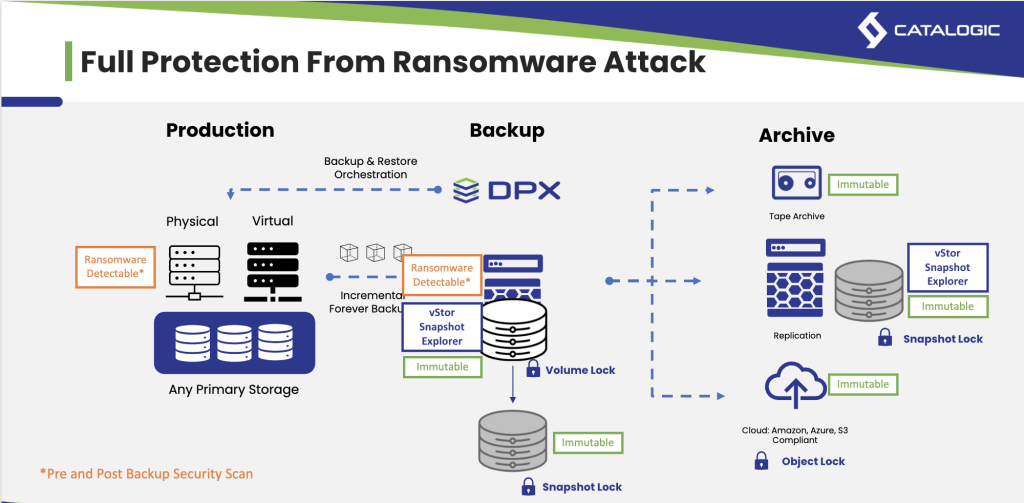
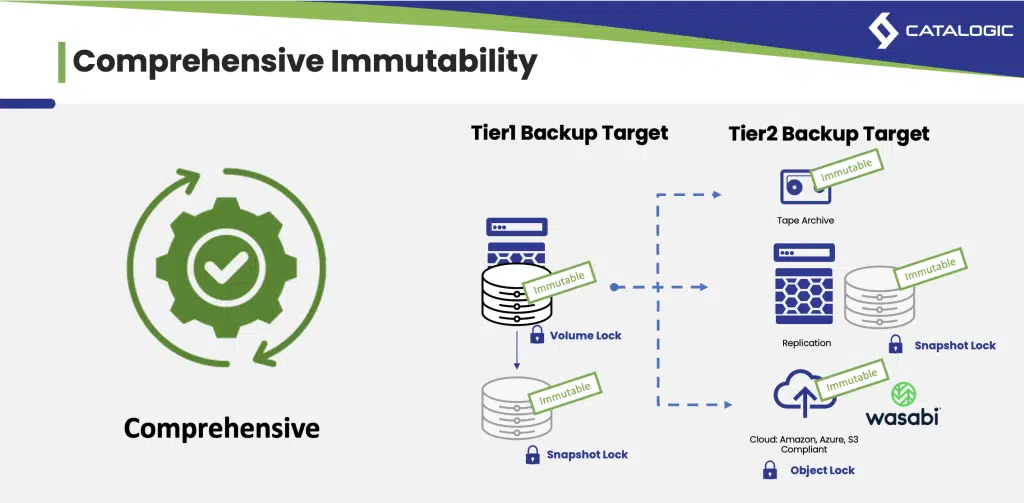
- Data Immutability: Ensuring backups can’t be altered or deleted without authorization is critical to protecting against data loss, corruption, and cyberattacks.
- Storage Optimization: Deduplication, block cloning, and compression help reduce the space required, especially valuable for large datasets.
- Scalability: Growing data demands a backup repository that can scale up easily and efficiently.
- Compatibility and Support: For smooth integration, the chosen storage solution should be compatible with the existing infrastructure, with support available for complex configurations or troubleshooting.
Storage Types for Backup Repositories
Here’s a closer look at four popular storage types for backup repositories: XFS, reFS, object storage, and DPX vStor, each offering unique advantages for data protection.
XFS with Immutability on Linux Servers
XFS on Linux is a preferred choice for many backup environments, especially for those that prioritize immutability.
- Immutability: XFS can be configured with immutability on the Linux filesystem level, making it a secure choice against unauthorized modifications or deletions.
- Performance: Optimized for high performance, XFS is well-suited for large file systems and efficiently handles substantial amounts of backup data.
- Storage Optimization: With block cloning, XFS allows for efficient synthetic full backups without excessive storage use.
- Recommended Use Case: Best for primary backup environments that require high security, excellent performance, and immutability.
Drawback: Requires Linux configuration knowledge, which may add complexity for some teams.
reFS on Windows Servers
reFS (Resilient File System) offers reliable storage options on Windows servers, with data integrity features and block cloning support.
- Immutability: While reFS itself lacks built-in immutability, immutability can be achieved with additional configurations or external solutions.
- Performance: Stable and resilient, reFS supports handling large data volumes, making it suitable for backup repositories in Windows-based environments.
- Storage Optimization: Block cloning minimizes storage usage, allowing efficient creation of synthetic full backups.
- Recommended Use Case: Works well for Windows-based environments that don’t require immutability but prioritize reliability and ease of setup.
Drawback: Lacks native immutability, which could be a limitation for high-security environments.
Object Storage Solutions
Object storage is increasingly popular for backup repositories, offering scalability and cost-effectiveness, particularly in offsite backup scenarios.
- Immutability: Many object storage solutions provide built-in immutability, securing data against accidental or unauthorized changes.
- Performance: Generally slower than block storage, though sufficient for secondary storage with infrequent retrieval.
- Storage Optimization: While object storage doesn’t inherently support block cloning, it offers scalability and flexibility, making it ideal for long-term storage.
- Recommended Use Case: Ideal for offsite or secondary backups where high scalability is prioritized over immediate access speed.
Drawback: Slower than block storage and may not be suitable for environments requiring frequent or rapid data restoration.
DPX vStor
DPX vStor, a free software-defined storage solution built on ZFS, integrates well with Catalogic’s DPX platform but can also function as a standalone backup repository.
- Immutability: DPX vStor includes immutability through ZFS read-only snapshots, preventing tampering and securing backups.
- Performance: Leveraging ZFS, DPX vStor provides high performance with block-level snapshots and Instant Access recovery, ideal for environments needing rapid restoration.
- Storage Optimization: Offers data compression and space-efficient snapshots, maximizing storage potential while reducing costs.
- Recommended Use Case: Suitable for MSPs and IT teams needing a cost-effective, high-performing, and secure solution with professional support, making it preferable to some open-source alternatives.
Drawback: Only provided with Catalogic DPX.
Comparison Table of Backup Repository Storage Options
| Feature | XFS (Linux) | reFS (Windows) | Object Storage | DPX vStor |
| Immutability | Available (via Linux settings) | Not native; external solutions | Often built-in | Built-in via ZFS snapshots |
| Performance | High | Moderate | Moderate to low | High with Instant Access |
| Storage Optimization | Block Cloning | Block Cloning | High scalability, no block cloning | Deduplication, compression |
| Scalability | Limited by physical storage | Limited by server storage | Highly scalable | Highly scalable with ZFS |
| Recommended Use | Primary backup with immutability | Primary backup without strict immutability | Offsite/secondary backup | Flexible, resilient MSP solution |
Final Recommendations
Selecting the right storage type for a backup repository depends on specific needs, including the importance of immutability, scalability, and integration with existing systems. Here are recommendations based on different requirements:
- For Primary Backups with High Security Needs: XFS on Linux with immutability provides a robust, secure solution for primary backups, ideal for organizations prioritizing data integrity.
- For Windows-Centric Environments: reFS is a reliable option for Windows-based setups where immutability isn’t a strict requirement, providing stability and ease of integration.
- For Offsite or Long-Term Storage: Object storage offers a highly scalable, cost-effective solution suitable for secondary or offsite backup, especially where high storage capacities are required.
- For MSPs and Advanced IT Environments: DPX vStor, with its ZFS-based immutability and performance features, is an excellent choice for organizations seeking an open yet professionally supported alternative. Its advanced features make it suitable for demanding data protection needs.
By considering each storage type’s strengths and limitations, you can tailor your backup repository setup to align with your data protection goals, ensuring security, scalability, and peace of mind.