Comparing VMware Backup and Replication: Understanding the Differences and Benefits
In our previous blog note titled Exploring VMware Backup Options: Enhancing Data Protection with Catalogic DPX, we delved into the various backup solutions available for VMware environments and how Catalogic DPX can elevate your data protection strategy. Building on that foundation, let’s now examine the critical differences between replication and backup within VMware vSphere environments and why it’s essential to distinguish between the two for a robust data protection plan.
The Essence of VMware Replication and Backup
At first glance, replication and backup might seem like two sides of the same coin—both are, after all, about safeguarding data in VMware and vSphere environments. However, the devil is in the details, and those details significantly impact how IT professionals approach data protection in VMware vSphere environments.
Replication is akin to having a real-time mirror of your data. It’s about creating an exact copy of your virtual machines (VMs) and keeping that copy in sync within VMware environments. This continuous synchronization ensures that, in the event of a disaster, the system can switch to a replica with minimal downtime. The key characteristics of replication include:
- Real-time Data Mirroring: Replication ensures that any changes made in the primary VM are immediately reflected in the replica, making it a critical component of VMware disaster recovery strategies.
- High Availability: It’s the go-to strategy for achieving minimal downtime and ensuring business continuity in VMware and vSphere environments.
- Rapid Recovery: In case of a failure, the system can quickly switch to the replica, significantly reducing the recovery time objective (RTO), a crucial metric in disaster recovery.
Backup, on the other hand, is the process of creating a historical copy of your data at specific intervals within VMware environments. These snapshots are stored and can be used to restore data to a particular point, should the need arise. Unlike replication, backups are not about real-time mirroring but about safeguarding against data loss over longer periods in VMware vSphere environments. Key aspects of backup include:
- Point-in-Time Snapshots: Backups capture the state of a VM at a particular moment, providing a historical record of data within VMware environments.
- Data Recovery: In the event of data corruption or loss, backups can be used to restore data to its original state, an essential aspect of VMware data protection.
- Flexible Retention Policies: Backup strategies allow for customized retention policies, ensuring that data is kept for as long as necessary, based on compliance requirements or business needs in VMware and vSphere environments.
The Differences between VMware Backup and Replication
Understanding the nuances between replication and backup requires a closer look at their core characteristics in the context of VMware vSphere and disaster recovery:
- Objective: Replication’s primary aim is to reduce downtime and ensure quick recovery, making it ideal for mission-critical applications in VMware environments. Backup focuses on data preservation, allowing for recovery from data corruption, user errors, and catastrophic failures in vSphere environments.
- Data Currency: Replicated data is current, often lagging just seconds or minutes behind the live environment in VMware vSphere. Backups, however, can be hours, days, or even weeks old, depending on the backup schedule.
- Storage Requirements: Replication demands more storage space and resources, as it maintains a ready-to-launch copy of VMs in VMware environments. Backups are more storage-efficient, especially when leveraging deduplication and compression technologies in vSphere environments.
- Recovery Point Objective (RPO) and Recovery Time Objective (RTO): Replication boasts a low RPO and RTO, making it suitable for applications where data loss and downtime must be minimized in VMware vSphere environments. Backups typically have higher RPOs and RTOs but offer more flexibility in recovery options.
Choosing between replication and backup—or more accurately, finding the right balance between them—is a strategic decision in VMware and vSphere environments. It involves weighing the criticality of applications, data loss tolerance, recovery time requirements, and budget constraints. In many cases, a hybrid approach that employs both replication for critical systems and backup for less critical data strikes the optimal balance in VMware data protection strategies.
Catalogic DPX: A Unified Solution for Replication and Backup in VMware Environments
Catalogic DPX stands out as a solution that appreciates the nuanced needs of VMware vSphere environments. Whether it’s achieving near-zero RTOs with replication or ensuring long-term data retention with backup, Catalogic DPX is the trusted solution for IT professionals navigating VMware backup and replication.
- Seamless Integration: Effortlessly integrates with VMware vSphere environments, ensuring a smooth data protection journey.
- Flexible Data Protection: Offers both replication and backup capabilities, allowing businesses to tailor their data protection strategy in VMware environments.
- Efficient Recovery: Whether it’s rapid recovery with replication or historical data retrieval with backup, Catalogic DPX ensures that your data is always within reach in VMware and vSphere environments.
Build Robust Backup Strategies with DPX
The debate between replication and backup is not about choosing one over the other but understanding how each one fits into a comprehensive data protection strategy in VMware vSphere environments. As we’ve explored, replication and backup serve different, yet complementary, purposes in the quest to safeguard data in VMware environments.
For those navigating the complexities of VMware vSphere data protection, Catalogic DPX offers a versatile and powerful tool. It’s designed to meet the demands of modern IT environments, providing peace of mind through both replication and backup capabilities.






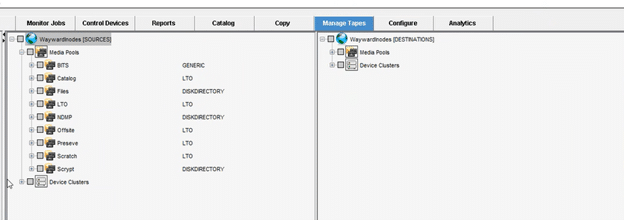 The tape migration process can also be helpful for moving media types of type DISKDIRECTORY
The tape migration process can also be helpful for moving media types of type DISKDIRECTORY